[ad_1]
Inside the Google Play Store several have been identifiedmalware-dropper for Android which disguise themselves as app updates, but are intended to recover and install banking Trojans that can steal the user’s login credentials and carry out unauthorized transactions.
Malware droppers represent a category of apps that are difficult to stem as they do not contain any malicious code and for this reason they are able to pass Google Play analyzes more easily when they are sent to the store for distribution. At the same time, users also do not suspect anything, as they make the advertised functionality available and perform their malicious work behind the scenes.
They are the researchers of Threat Fabric ad having discovered the new group of droppers, also signaling an increase in the diffusion and use of these tools precisely because of their effectiveness. The first campaign identified by Threat Fabric dates back to the beginning of October and spreads the banking trojan known as SharkBota malware that steals login credentials to online banking services by exploiting false login requests disguised as login forms to legitimate websites, or by exploiting keylogging techniques, stealing and hiding SMS messages and taking remote control on a mobile device.
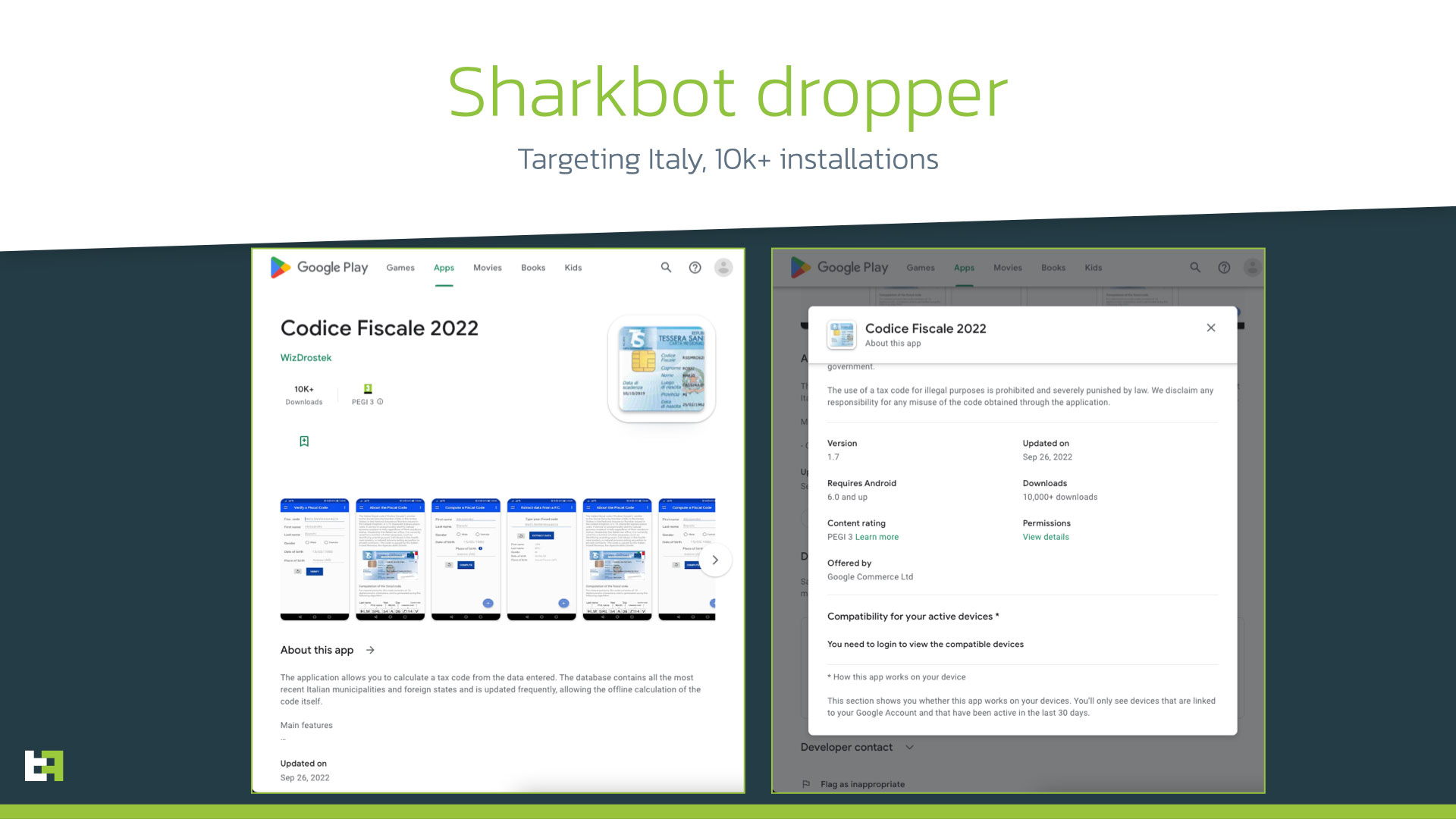
The researchers specifically spotted two seemingly harmless-looking “dropper” apps, one of them closely affects the Italian public: it’s about “Tax Code 2022“, an app that is used to calculate the tax code of any citizen from their personal data. Tax Code 2022 has been downloaded 10 thousand times. The other app” File Manager Small, Lite “to manage files on the device.
When the user installs one of these two apps, they are eventually asked to proceed with the installation of a bogus update, which is actually the actual SharkBot malware. The request is disguised as a Google Play page, tricking the user into tapping the “Refresh” button.
The version of SharkBot that is installed via Tax Code 2022 specifically targets Italian banking institutions, making use of fake login overlays, intercepting SMS for two-factor authentication codes and exploiting keylogging and cookie theft features. As for File Manager Small, Lite, on the other hand, the version of SharkBot is aimed at a wider range of targets, also including banking institutions in the United Kingdom, Spain, Poland, Austria, Australia and the United States.
Another malware-dropper campaign concerns Vulturalso a banking trojan that is distributed through the Zetter Authentication apps (10,000 downloads), My Finances Tracker (1,000 downloads) and Recover Audio, Images and Videos (100,000 downloads).
Threat Fabric notes that distributing malware via droppers on Google Play is the simplest way to reach victims with little use of resources. There is, however, a weakness in this technique, which is the need to require manual action from the victim. However, masking strategies often prove to be very effective, misleading users.
.
[ad_2]
Source link
