[ad_1]
A common technique among the operators of malware to spread their attack tools that of cloning popular software websites and exploiting them to distribute trojan versions of the software to users who they thus believe that they are making a safe and legitimate download.
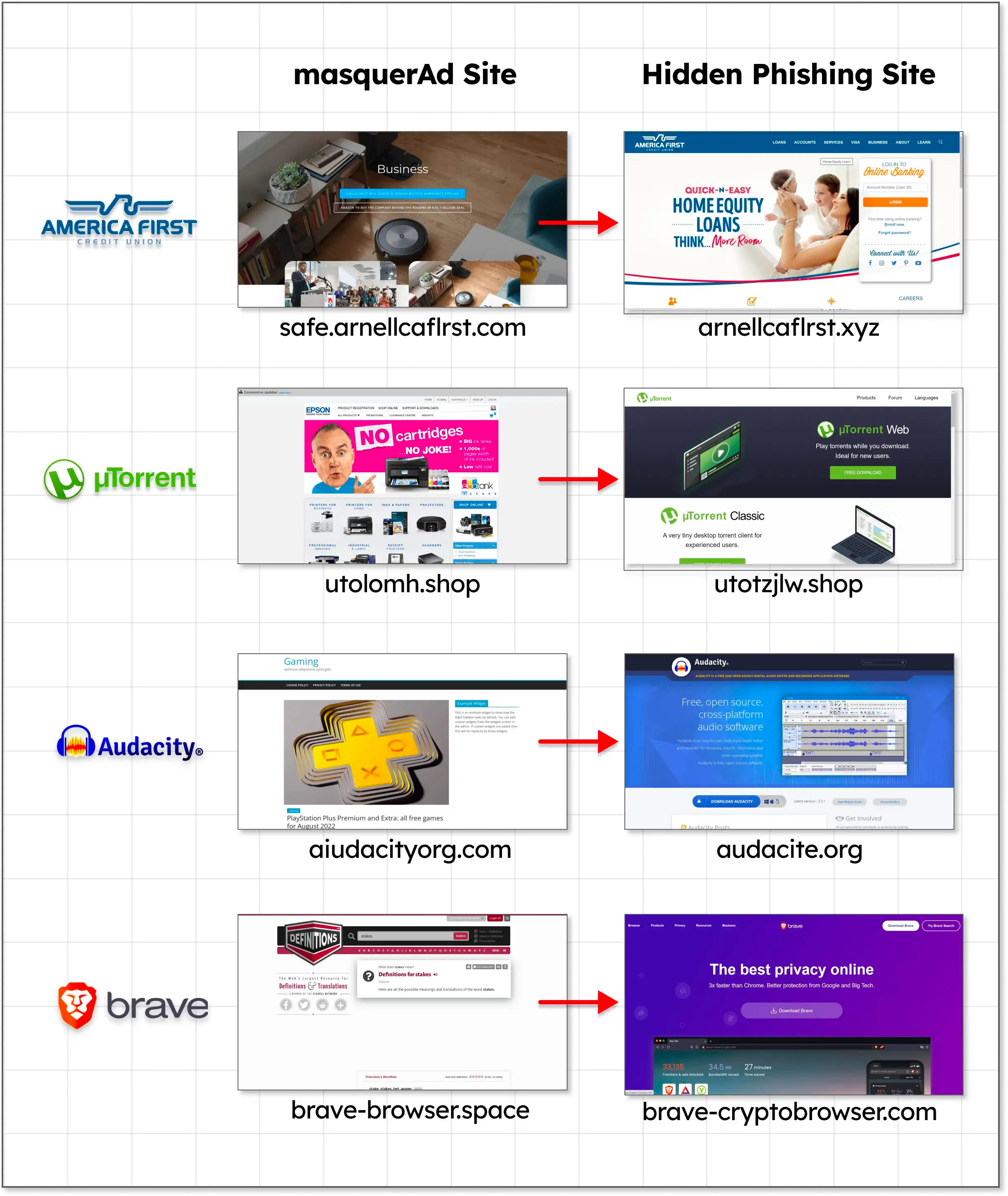
Among the software that are mostly used for this purpose are Grammarly, MSI Afterburner, Slack, Audacity, μTorrent, Libre Office, Teamviewer, Thunderbird, Brave, OBS, Dashlane, Ring and AnyDesk. Some of the malware spread using this technique are variants of Raccoon Stealera version of Vidar Stealer and another malware loader IcedID.
Guardio Labs sheds light how users are exposed to these websites, which are promoted to a wide audience taking advantage of Google Ads advertising campaigns.
The Google Ads service allows advertisers to promote, for a fee, your sites among the Google search results, placing them in the first place of the results page and often above the official website of the project you are researching. The links that are promoted for a fee are also accompanied by a small mark that identifies them as ads, a detail that is often overlooked by the user who, on the contrary, is convinced they are dealing with a legitimate site.
To limit the risks Google provides a level of countermeasures: If the target site is detected as dangerous, the campaign is blocked and the ads removed, thus limiting the effective potential of this strategy. However Threat actors have found a way around this control system.
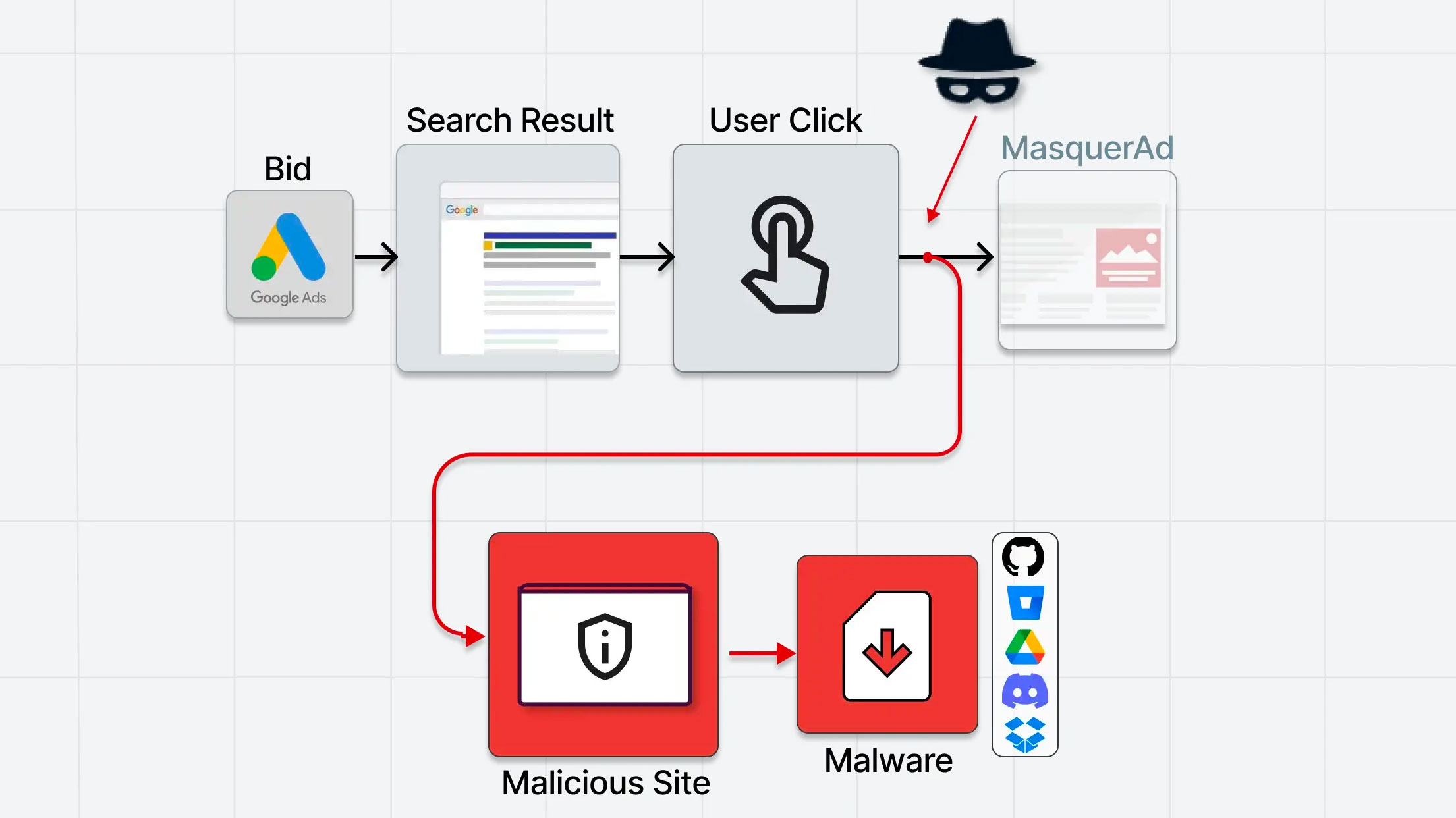
The ploy is to lead victims who click on the ad to a harmless site created by the threat actor, which Guardio calls “masequerAd“, and subsequently redirect them to a malicious site impersonating the legitimate resource sought by the user.
“The moment these masquerAd sites are visited via the search engine ad, the server immediately redirects the visitors to the rogue site and from there to the malicious payload. These rogue sites are virtually invisible to visitors who don’t reach them via the stream promotion that exploits the masquerAd site by showing it as legitimate to crawlers, bots, casual visitors and Google countermeasures” explains Guardio Labs.
The payload, in zip or msi format, is downloaded from file sharing services such as GitHub, Dropbox or the Discord CDN, thus preventing the antivirus running on the victim’s computer from preventing the download. The researchers cite as an example a campaign monitored last November through which the Raccoon Stealer malware was distributed together with a legitimate version of Grammarly: the trapped users then got what they were looking for, with the “gift” of a malware that install behind the scenes without a trace.
The Guardio Labs report concludes with the clarification of a key concept: “Security is a matter of trustthat’s why we constantly turn to reliable and trusted suppliers for our daily activities on the web. […] This “masquerAD” concept
[abusa] of the trust we sometimes blindly place in Google and its search results”.
It comes from here the basic approach to security known as “trust no one”, that is, don’t believe anyone and use that extra pinch of scruple, almost bordering on paranoia, every time you perform an action on the web. In this specific case, always check the URLs from which resources are downloaded, pay attention to any anomalous characters (so-called typosquatting) and when searching on Google, avoid clicking on the ads at the top of the list of results.
.
[ad_2]
Source link
