[ad_1]
The apparently more trivial and less sophisticated hacking techniques are often the most effective in overcoming the defenses, even advanced ones, of companies. Let’s think about phishing, for example. Or to the spread of Word or PowerPoint documents containing malware. A trend, the latter, somewhat dormant lately, also because companies have better trained their employees and security solutions have begun to inspect these documents as well.
Since last December, however, Proofpoint researchers have noticed a significant increase in attacks via OneNote documents. The trick is always the same: a document pretending to be an invoice, information on shipments or the like containing cleverly disguised attachments. Which, when launched, activated the virus payload.
The evolution of attack techniques explained by Proofpoint
Between December 2022 and January 2023, Proofpoint researchers detected an increasing number of cyberattacks that exploited Microsoft OneNote documents containing viruses.
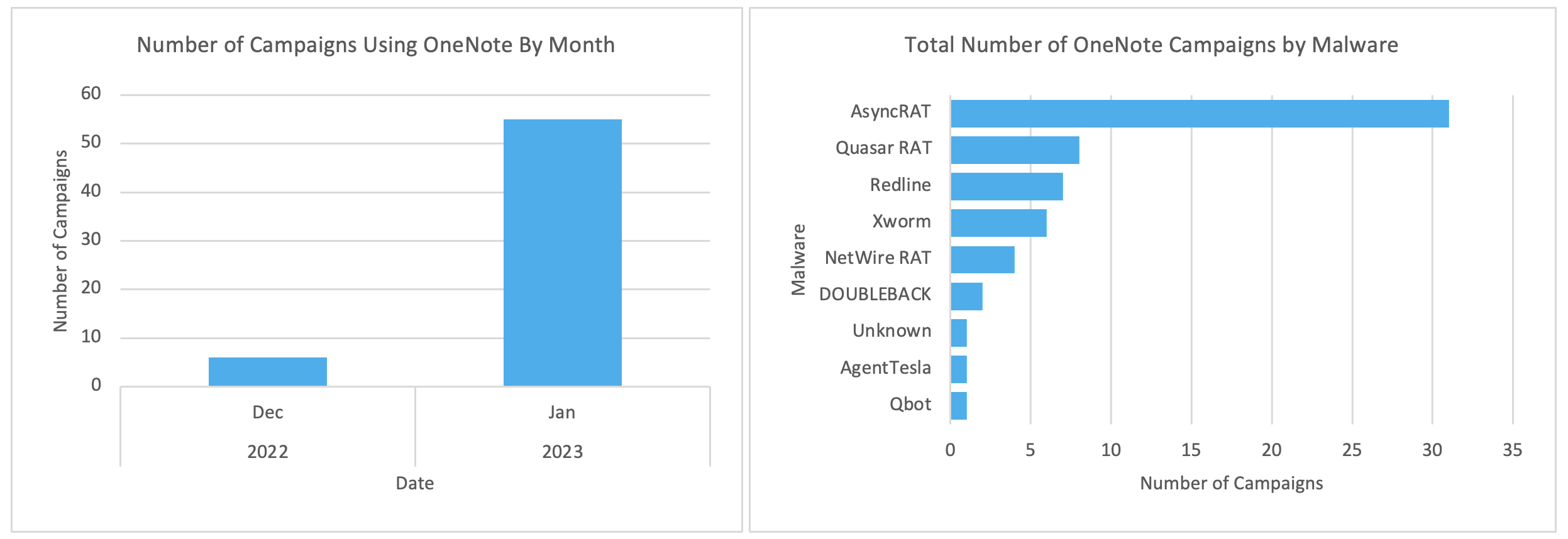
In December, in particular, they attempted to distribute the AsyncRAT malware, while in January 2023 the activities intensified and from the 6 campaigns of the previous month they reached 50as well as other malware, including Redline, AgentTesla and DOUBLEBACK, Qbot, Netwire and XWorm.
According to the researchers, these are attempts to circumvent the defenses that Microsoft had set up for some time, disabling the default activation of macros in these applications. This is where cybercriminals started exploiting other file types, such as VHDs, virtual disks used by virtualization platforms, CHMs (compiled HTML), and lately OneNote files with the .one extension.
The most striking thing, however, is the fact that more than one security solution was unable to detect them. But how did attackers hide malicious code? The trick is to create credible documents, as in the case of phishing emails, linking the execution of files attached to buttons on the document or masking them behind images: a double click is enough to execute them. It must be said that OneNote warns the user with a message before execution: only by giving the OK does the program containing the malware actually start.
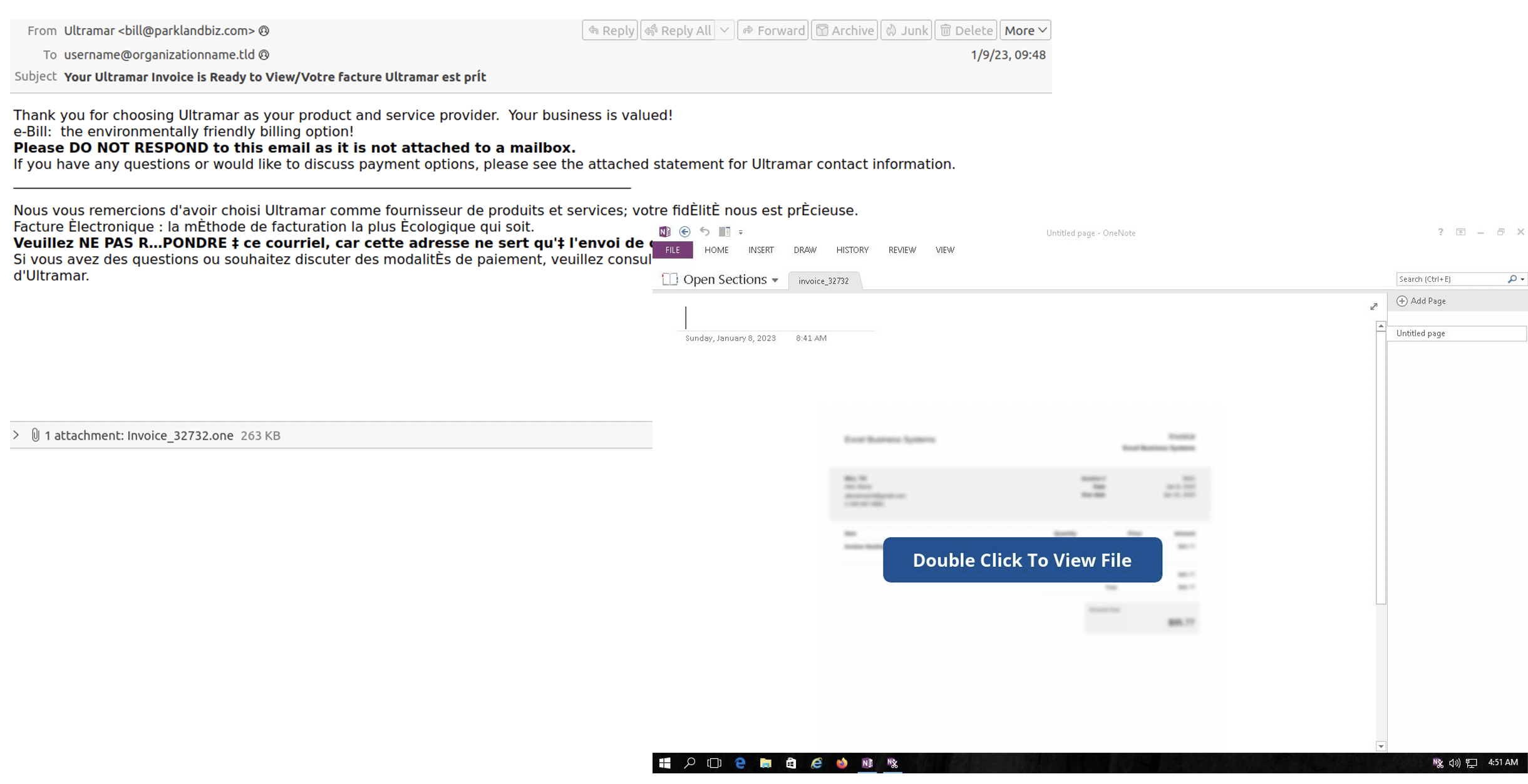
According to Proofpoint, among those responsible there would be the TA577 group, but it is not the only one and the activities are attributable to several actors.
“For months, cybercriminals have been testing new tactics, techniques and procedures (TTP) to spread malware via email.”the researchers explain.”Our research shows that these recent activities are using Microsoft OneNote documents to spread their malicious content, a method that seeks to creatively bypass existing antivirus detections. It is worth noting that in order for the infection to be successful , the user should interact with the OneNote document and ignore warnings that the content may be harmful.Based on the increase in the use of OneNote in campaigns and the diversity of payloads, it is likely that in the future we will see more actors adopt similar methods in campaigns”,
.
[ad_2]
Source link
