[ad_1]
The theft of sensitive data on the web a sore that is not easy to solve and above all very extensive given the ease with which it can be achieved. Today, more and more malicious people try to steal identities, hack emails and social profiles, but also and above all steal credit card informationto be able to clone them or make purchases without the owner’s knowledge.
Precisely on the basis of this and the credit card data we use on the web to make purchases on various online stores, there is a practice widely used to speed up the operation that would be better avoided from now on. It happens more and more often in fact than save credit card information in the browser cacheby Google Chrome. A convenient practice that allows users to find payment data immediately at hand without having to re-enter the credit card number each time. A safe operation at least until today given that the researchers of the teamProofpoint Threat Insightshave discovered a new malware capable of stealing data stored in the cache memory of the Chrome browser.
Chrome: This is how data-stealing malware works
The discovery came from the researchers of the teamProofpoint Threat Insightswho had already raised the alarm a few weeks ago. In this case it appears to be a new form ofEmotetone of the most widespread and infesting malware of recent years, ready to steal sensitive credit card data such as number, holder and CVV code stored in the cache of the Google Chrome browser.
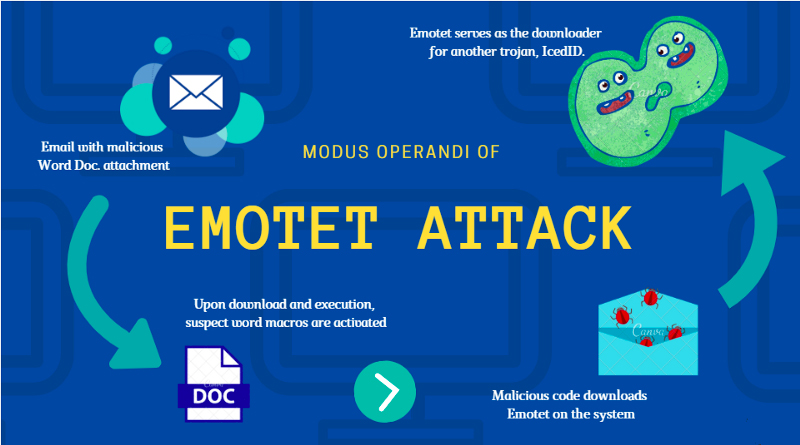
Its simple operation but also effective for criminals. The malware, in fact, after stealing the information, would send it to different command and control servers C2 than those already used in general by the same Emotet module to steal card data. This would make it even more difficult to trace the perpetrators of the cyber theft.
A serious threat and that fortunately at the moment it would only target data cached in the Google Chrome browser. The new malware risks having far more unpleasant consequences in the future. We know in fact that in the past the infections caused byEmotetthey can introduce even new ones into infected devicesransomware, programs that make some data or functionality of the device inaccessible. In this case, the attackers could then request the payment of a ransom, almost always in cryptocurrency, to return or make a device work again.
Emotet: how to defend against malware?
Unlike other viruses already known and therefore modern antivirus are able to block, in this case the most complex malware and therefore can divert from antivirus. In this case, therefore, the need to consider some precautions to be taken to avoid the theft of sensitive data must be implemented. First of all it is clear that it is better not to save credit card data in the browser cache, but enter them by hand each time. Not only because according to experts it is necessary to pay close attention to the links on which you click because theseEmotet malwarethey typically spread via email, using dangerous links and attachments.
There are conflicting opinions on the origin of Emotet. The Intelligence of Australia, Canada, New Zealand, the United Kingdom and the United States had compared him to Russian hackers who, after the outbreak of theconflict in Ukrainethey would have exacerbated the attacks. The first time Emotet appeared in 2014 as a banking trojan then later modules were added that allow it to steal the sensitive data of the poor unfortunates.
.
[ad_2]
Source link
