[ad_1]
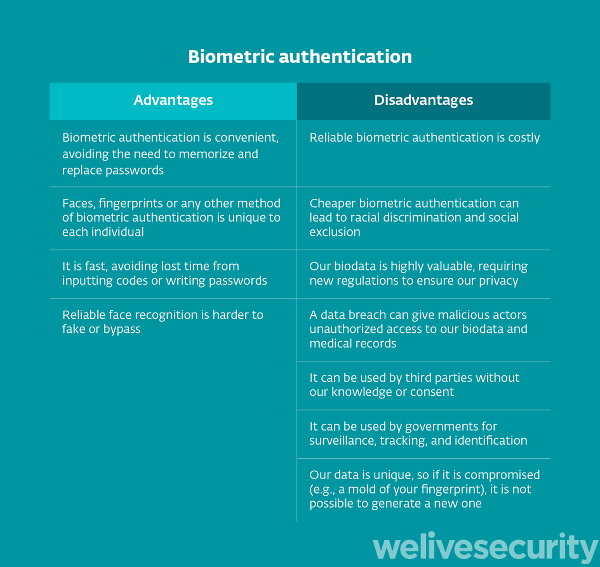
Passwords are the most popular way to verify user identity and allow people to access services and data, but they are not the safest approach. In addition to being inconvenient to use, they are unable to guarantee too high a level of security, so much so that a high percentage of cyber attacks start from stolen credentials.
In recent years, various forms of biometric authentication, such as fingerprint, facial or voice recognition, are becoming more and more popular. They are considered extremely safe and, above all, comfortable and fast, so much so that they are an integral part of the PSD2 directives for the security of digital payments.
But what are the various biometric authentication methods and what are their characteristics? ESET took stock of the situation.
Fingerprints: an old but still effective method
The Fingerprints they have been used for a lifetime to verify the identity of an individual. Fingerprints are among the first clues that are sought at a crime scene, and they have a great advantage: the chance that two people will share the same fingerprints is close to zero. Consequently, they have always been used on identity documents and, lately, they are also used for unlocking smartphones and accessing computers.
There are various technologies to recognize fingerprints, all of which are very reliable: optical sensors, capacitive or ultrasonic sensors. The limit of this recognition system is that if they were to be stolen, it would be a huge problem: unlike a password, they cannot be replaced or changed. For this reason, companies tend to use extremely secure systems to manage: in the case of Apple, Google and Samsung, for example, the fingerprints are never uploaded to the servers, but are kept in encrypted form on the device itself, so as to minimize the risk of them being stolen.
Facial recognition
Until about 15 years ago, facial recognition was considered science fiction but today we almost take it for granted. We can use it to unlock the phone, as well as to access the computer, thanks to authentication systems such as Windows Hello.
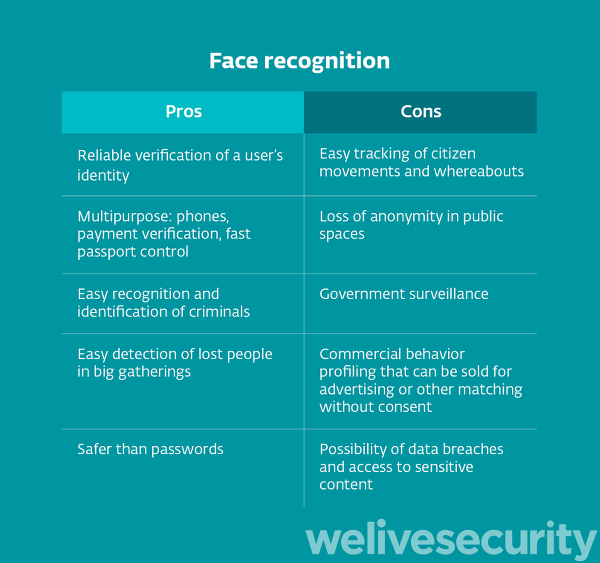
Also in this case, the security is very high and a photo is not enough to fool the sensors. Authentication is not based on simple images, but measures unique characteristics of each individual, such as the distance between the eyes or the distance between the chin and the forehead. Not only that: the most advanced authentication systems (including Windows Hello) use 3D cameras, so as to obtain more information from the face and make identification more precise.
But there is a problem: facial recognition lends itself to abuse. In particular, if the system is managed by a government not very fond of freedom. The huge spread of surveillance cameras in every public place combined with the enormous advances made in the field of AI would allow for potential mass surveillance. Paranoia? Unfortunately not, in China its use is already widespread.
Vocal recognition
A third way to identify a user is to use voice. Even this approach years ago was considered pure science fiction (it was used, for example, in the movie I Lords of the Scam) but today we use it every day with voice assistants such as Siri, Alexa or Google Home, increasingly popular in homes.
However, they are not so effective and safe compared to the methods mentioned above: who has never seen the assistant take “initiative” without having given any command? Of course, algorithms are increasingly effective in reducing errors and uniquely recognizing a voice, but there is still a long way to go in this respect.
The future of biometric authentication
With the spread of wearable devices, according to ESET, more and more secure methods will emerge to verify identity: the rhythm of breathing, heartbeat, sleep patterns, but also the way we move, for example when we take the phone out of our pocket or how we walk.
.
[ad_2]
Source link
