[ad_1]
There are three main themes that emerge from the Global Threat Report 2023 Of Crowdstrike, a study that analyzes how the cybercrime scenario has taken place in the past year. A year which was marked by the war between Russia and Ukraine, a conflict which inevitably also spread into cyberspace, on both sides. And it has seen escalating actions by various groups. Groups linked to the two warring nations, trying to sabotage each other, but not only. Crowdstrike has seen an increase in activity from China-nexusa group supposedly linked to the Chinese government, which has stepped up its espionage operations against Taiwan.
Another growing trend is that of malware-free attacks, which go from 62% in 2021 to 71% in 2022, which do not use malware but exploit other techniques, starting with the exploitation of unpatched vulnerabilities. This allows attackers to better hide in their victims’ systems and stay inside them longer.
The third key theme is that of cloud attacks, grown by 95%.
Malware? He’s not the worst enemy of security experts
We tend to think that any cyber attack is due to malware. Often also making fun of, or harshly criticizing, the employee who by mistake clicked on the link of the phishing email or opened the attachment containing a virus. However, the reality is different: the majority of intrusions, 71% according to the Crowdstrike report, do not leverage malware. And how then do the attackers breach the defenses? Exploiting vulnerabilities that are not patched in time, or in some cases even zero day flaws. A more complicated approach in some respects, because it requires the attacker to have high computer skills, but more effective, given that it makes it easier to circumvent security controls and, above all, to maintain persistence in the systems of unsuspecting victims.
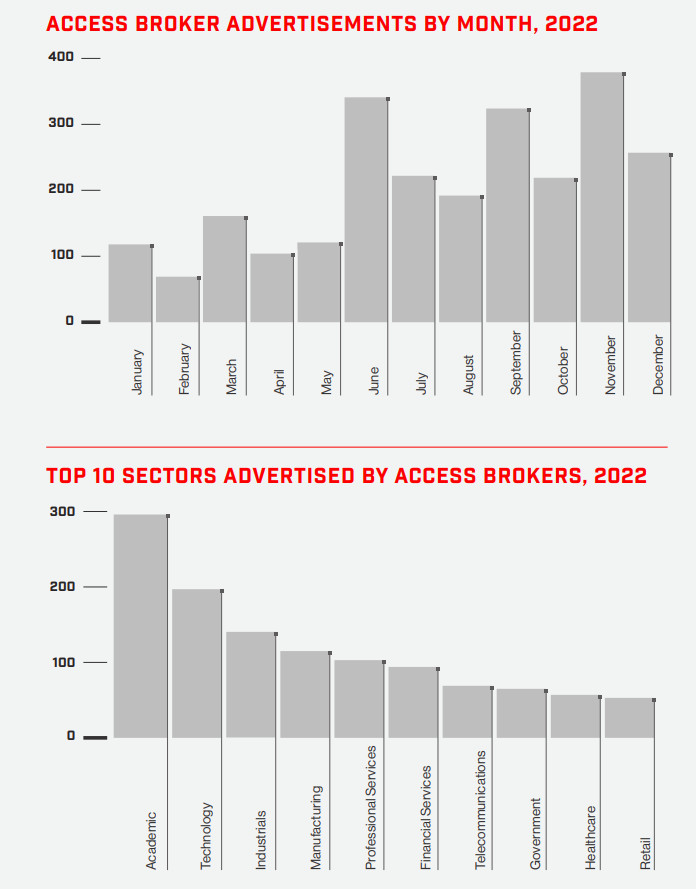
Not all attackers are extremely technically proficient, but Access Brokers come to their rescue,”those who do the dirty work“, he explains Luca Nilo Livrieri, Senior Manager, Sales Engineering – Southern Europe at Crowdstrike. These are teams of hackers who go looking for vulnerable systems and then resell the credentials to third parties, who then take care of extorting money from the victims.
Who are Access Brokers?
But who are access brokers? According to Livrieri “there is no particularity or geographic characterization of the access broker“. Among the most active groups are those from Turkey, as well as teams based in Russia or Eastern Europe, “but we have also seen them in the USA and in South America“. Few, however, are the groups that act from Italy. The few identified are mostly lone wolves who act as hacktivists, and in fact after the outbreak of war in Ukraine we have seen an intensification of these actions.
Livrieri does not hide the fact that Crowdstrike is a western company, inevitably linked to the United States, a fact which inevitably conditions the analysis to some extent. This means that we tend to talk a little less about sabotage and espionage operations carried out by groups linked to Western governments against Russia or China even if “as far as cybercrime is concerned, we don’t look anyone in the face“.
This is inevitably an issue that involves all companies dealing with security related to the West, not just Crowdstrike. And, indeed, if we remove the famous Stuxnet, there is rarely room for cyber operations conducted by our allies.
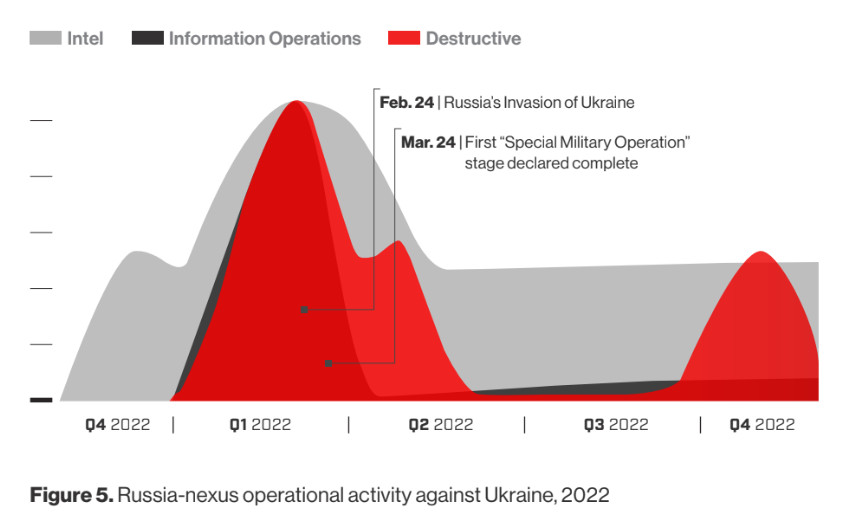
Livrieri also highlights another theme linked to the cyber war between Russia and Ukraine: the general media talk a lot about “physical” attacks, with bombs, drones and tanks, less so than computer ones, which certainly are not lacking, given that above all Russia has extremely competent groups in this respect. According to Livrieri “little is said about it because there is little knowledge of the matter and because predictions of the destructive trend have been questioned. In the first quarter, we saw many attacks on network infrastructure or specific assets such as government databases. Now that the war is going on, both groups [ucraini e russi, NdR] they try to exploit cyber attacks more to steal information than to sabotage the adversary“.
Two-factor authentication needs to be implemented better
Another key aspect that emerges from the report is how the cloud is increasingly under attack and the operations conducted against these infrastructures have tripled. Understandable, considering that more and more companies and government agencies are moving data and workloads to the “cloud”, but it is surprising that these infrastructures are violated so frequently, given that they are considered strategic and, on paper, logins should be protected by multi-factor authentication or Single Sign On (SSO) systems and zero-trust approaches.
To break a multi-factor authentication, however, it is not necessary to have who knows what resources or knowledge. One of the most common methods, in fact, is to hammer the users of the services with constant requests for access. By dint of sending notifications on mobile devices, sooner or later someone will give the OK, either out of exhaustion or out of distraction, thus giving the attacker the green light.
According to Livreri, this problem could be at least partially limited by using MFA more effectively. Some companies have rather complex access procedures, which require entering multiple codes, on multiple occasions, several times a day. Limiting the need to authenticate multiple times could help mitigate these types of breaches.
The new actors of e-crime and their behaviors. Encrypt files? It’s getting out of fashion
Crowdstrike intelligence has identified 33 new adversaries in 2022, 20 of which belong to SPIDERS, the name CrowdStrike conventionally uses for eCrime opponents. Among the new opponents also tracked BEARs (Russia-Nexus opponents), GOSSAMER BEAR, highly active during the first year of the conflict between Russia and Ukraine, targeting government research laboratories, military suppliers, logistics companies and non-governmental organizations (NGOs). CrowdStrike also featured the first Syria-Nexus adversary, DEADEYE HAWKpreviously tracked by Crowdstrike as the hactivist DEADEYE JACKAL.
Regarding ransomware, it should be noted that attackers are less and less interested in encrypting files. The reason is simple: the threat of publicly releasing the stolen information is more than enough to convince victims to give in.
.
[ad_2]
Source link
