[ad_1]
The NAS produced by would be tens of thousands QNAP extension to be affected by one vulnerability which would be easy to exploit and which would give total control of the device to the attacker. QNAP has already issued a corrective patch, but there would be very few devices on which it has already been installed.
New severe vulnerability for QNAP NAS
The vulnerability, which got a severity score of 9.8 out of 10is indicated by the number CVE-2022-27596 and makes it possible to make an attack of SQL injection for which no permissions are needed and which allows to gain complete control of the victim device. Devices running QTS OS with versions lower than are affected 5.0.1.2234 and those with QuTS hero versions prior to h5.0.1.2248.
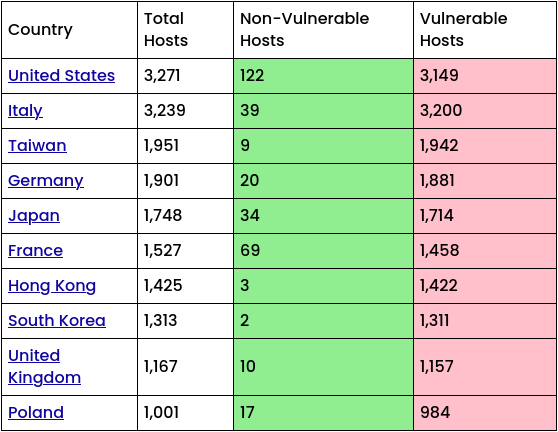
Censys verified that there are 67,415 QNAP devices directly accessible on the network, but only 30,250 of these communicate the version of the operating system used. Of these 30,250, 98% were vulnerable; on the other hand, only 557 were equipped with an operating system with the patch already applied. This means that nearly 30,000 devices, and probably many more, are vulnerable to attacks.
It is significant to note how Italy appears, in the Censys survey, to be the second country in the world for the number of devices detectedwith 3,239 publicly accessible NAS of which just 39 are patched.
Beyond the immediate application of the patch, it is advisable to disable Internet access to the NAS to avoid such problems. In fact, there are many cases of malware that, over the years, have targeted QNAP devices accessible via the Internet: among others, we recall Checkmate, Deadbolts And Qlocker.
.
[ad_2]
Source link
